



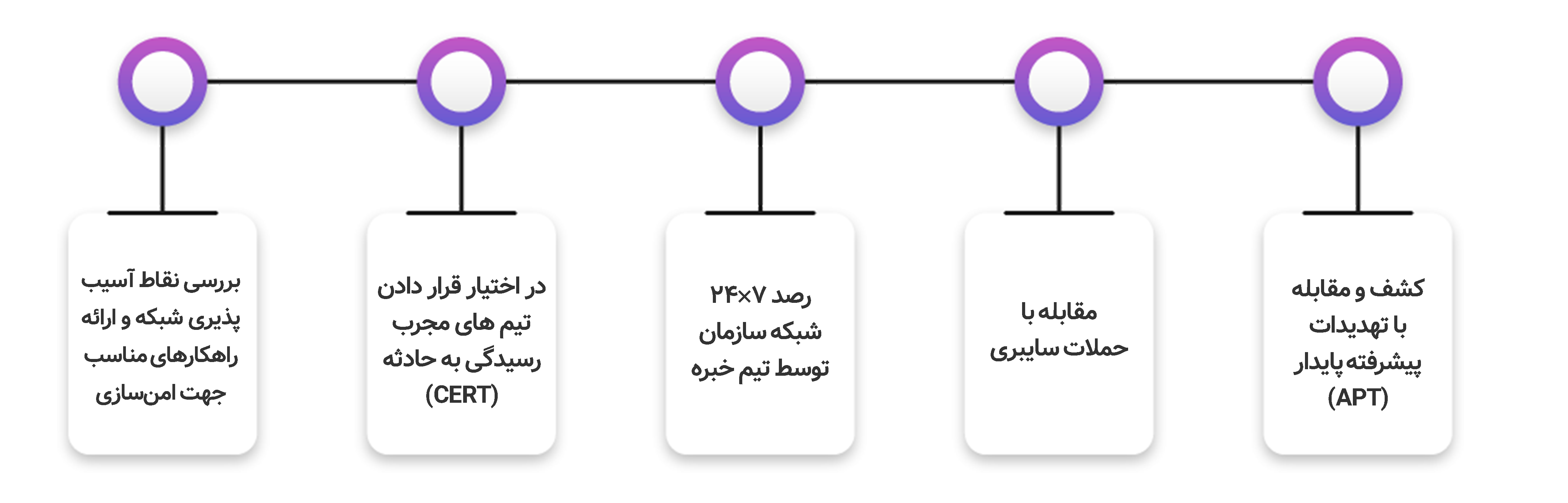
به نظرتان ورود موفق پس از پنج بار اشتباه زدن رمز عبور در نیمههای شب یا استفاده از یک ابزار بررسی ترافیک شبکه، نشانه چیست؟ احتمال وقوع یک حمله سایبری یا تلاش یک ادمین سختکوش در حال رفع مشکل شبکه ؟ آیا یک ضد بدافزار به تنهایی توانایی تشخیص چنین حملاتی را دارد؟ طبیعتا بررسی و تشخیص این نوع مسائل تنها توسط افراد متخصص امکان پذیر است که در این راستا متخصصین امنیت سایبری پادویش می توانند این نوع حملات هدفمند و بدافزارهای ناشناخته را شناسائی نمایند.

|
سطح هشدار |
زرد | نارنجی | قرمز | سیاه |
|
اعلام هشدار از طریق تماس |
||||
|
زمان تماس |
_ | ساعت کاری (۷صبح تا ۷ شب) |
۷×۲۴ | ۷×۲۴ |
|
مهلت آغاز بررسی |
_ | ۱ هفته | ۱ روز | ۱ ساعت |
|
اعلام کتبی هشدار |
_ |
| قابلیت | MDR Optimum | MDR Base/Select | MDR Expert |
|
نظارت ۷در۲۴ |
|||
|
تیم متخصص با تجربه بررسی حملات سایبری اخیر کشور |
|||
|
عمق سنسورهای پیشرفته |
متوسط | عمیق | عمیق |
|
اعلام هشدارهای امنیتی |
|||
|
اعلام هشدار از طریق پیامک/تماس |
|||
|
اعلام هشدارهای مهم به صورت کتبی |
|||
|
شکار تهدیدات فعال |
|||
|
سطح سرویس تضمین شده |
|||
|
نگهداری هشدارها تا یکسال |
|||
|
گزارش دورهای وضعیت شبکه |
|||
|
عملیات فارنزیک |
|||
|
اعلام نقاط ضعف و قابل بهبود شبکه |
_ | ||
|
نگهداری لاگهای خام به مدت تعیین شده توسط سیاست سازمان |
_ | ||
|
دسترسی به سامانه وب Padvish EDR |
_ | ||
|
پویش فایل های اجرایی با Multi-AV |
_ | انتخابی | |
|
امکان ارسال فایل های اجرایی به سندباکس |
_ | انتخابی |

برای دریافت راهنمایی در زمینه خرید و پشتیبانی
محصولات پادویش با شماره تلفن زیر در تماس باشید:
۰۲۱-۴۳۹۱۲۰۰۰
واحد فروش محصولات سازمانی:
reseller@amnpardaz.com
واحد فروش محصولات خانگی:
retail@amnpardaz.com
پشتیبانی محصولات پادویش:
support@amnpardaz.com
درباره پادویش بیشتر بدانید