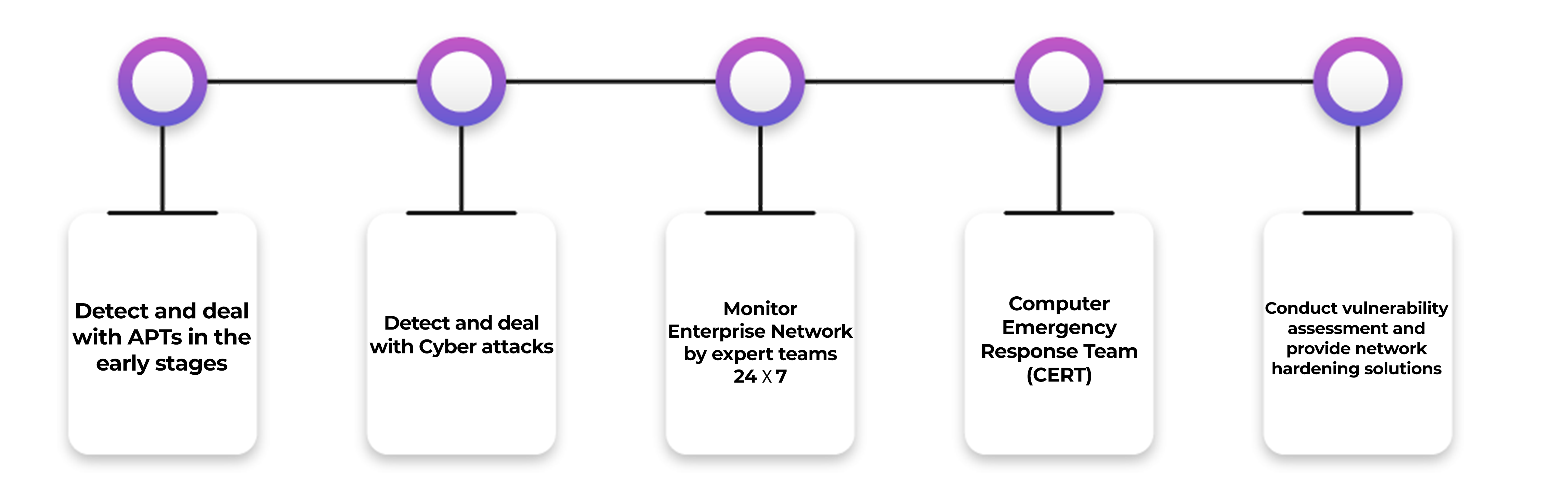
An anti-malware tool alone may not be sufficient to detect the intent behind some suspicious activities. For example, a successful login after multiple incorrect password attempts, especially during unusual hours, can indeed be indicative of a potential cyber attack. However, it's crucial to consider alternative scenarios, such as the efforts of an administrator trying to fix a network problem. Detection of these issues requires the expertise of cybersecurity professionals. Padvish's cybersecurity experts are well-equipped to detect targeted attacks and unknown malware

|
Alert Level |
Yellow | Orange | Red | Black |
|
Call notification |
||||
|
Time to call |
_ | Working hours
(7 a.m. to 7 p.m.) |
24×7 | 24×7 |
|
Checking requirement |
_ | 1 Week | 1 Day | 1 Hour |
|
Alert written notice |
_ |
| Features | MDR Optimum | MDR Base/Select | MDR Expert |
|
24×7 Monitoring |
|||
|
An expert team with the experience of investigating the recent cyberattacks |
|||
|
The depth of advanced sensors |
Medium | Deep | Deep |
|
Security alert notification |
|||
|
Alert notification via text message/call |
|||
|
Alert written notice |
|||
|
Active threat hunting |
|||
|
Guaranteed service level |
|||
|
Storing alerts for up to one year |
|||
|
Periodic network status report |
|||
|
Forensics |
|||
|
Network security status assessment |
_ | ||
|
Reporting the weaknesses and improvable aspects of the network |
_ | ||
|
Storing raw logs for the period determined by the enterprise policy |
_ | ||
|
Access to Padvish MDR website |
_ | ||
|
Scan executable files with Multi-AV |
_ | * | |
|
Ability to send executable files to the sandbox |
_ | * |
Download Padvish MDR Brochure